Awesome link branding!
Promote anything you need each time you share a link and grow your audience. Easy, contextual and free!
Prefer other ways of sharing?
You can use our Bookmarklet to share links to any social network or brand links manually in your dashboard .
Try 
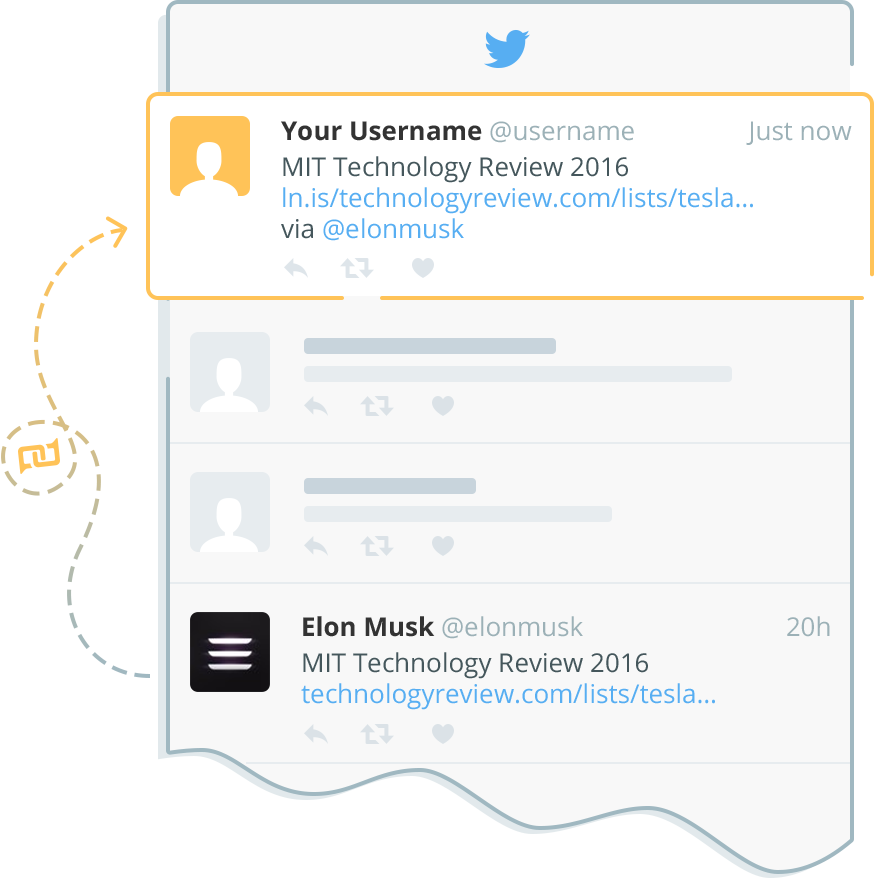 We pick the most engaging tweets
We pick the most engaging tweets from your newsfeed and post them on your behalf
Have no time for routine?
Need fresh content?
Or just going on vacation?
Try Convey, our new service helps you support your social activity and grow your audience by posting the most trending news for you on a daily basis.
Don't take our word for it
800,000 people are using Linkis to boost their online presence and encourage interaction with their readers.